Our Services.
We partner with professional cybersecurity businesses to meet your needs.
We promise to provide help to your highest level of satisfaction.
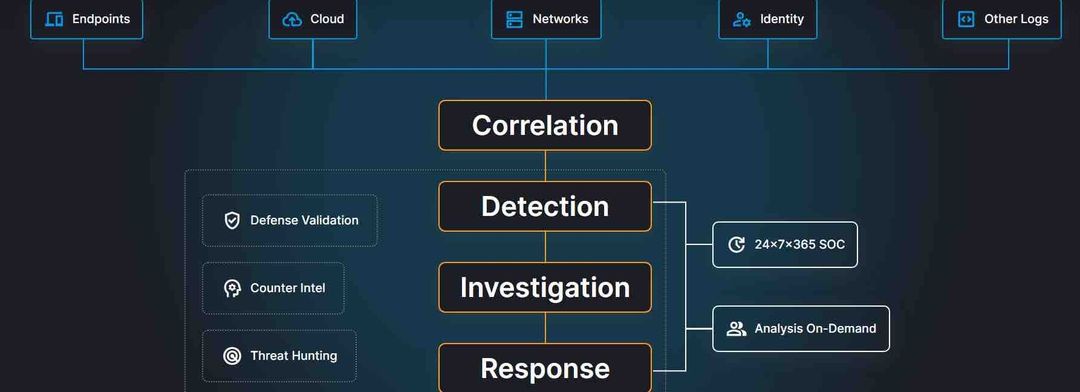
SOCaaS.
SOC-as-a-Service is just one of the many services that Allied's partners offer.. When you need it most, you can rely on our Security Operations Center (SOC) Cyber Analysts to answer the phone live, 24/7, with knowledge, assurance, and thorough response. Our Security Operations Center staff goes well beyond keeping watch over the glass. We provide round-the-clock security monitoring, hypothesis-driven threat hunting, interruption of threats, and containment of
threats, and full response.
EDR/MDR/XDR.
EDR (Endpoint Detection and Response), MDR (Managed Detection and Response), and XDR (Extended Detection and Response) are all cybersecurity solutions that focus on threat detection and response.
Penetration Testing.
Penetration testing is a proactive approach taken by organizations to identify vulnerabilities in their security systems. It involves simulating realistic attack scenarios to evaluate the strength of an organization's defenses and identify any weaknesses that could be exploited by cybercriminals.
Vulnerability Scanning.
Vulnerability scanning is a critical component of cyber security that helps to identify potential weaknesses in an organization's computer network and systems. It involves using specialized software tools to scan the network and identify any vulnerabilities that could be exploited by cybercriminals.
Employee Security Awareness & Education.
Employee security awareness and education are critical components of cybersecurity in any organization. With the proliferation of cyber threats, it is important that employees are trained on safe practices to prevent cyberattacks. Cybercriminals often target employees through email phishing, social engineering, or by exploiting vulnerabilities in software applications.
CASB.
A Cloud Access Security Broker (CASB) is a security control solution that is designed to protect cloud-based data and applications. CASBs provide a centralized location for monitoring cloud applications, enforcing security policies, and detecting potential threats.
SASE.
Secure Access Service Edge (SASE) is a new approach to cybersecurity that incorporates a cloud-based security architecture with connectivity capabilities. SASE addresses the security needs of modern organizations by providing comprehensive and integrated protection for their network, users, and applications.
Email Security.
Email security is an important aspect of cyber security, as email is one of the most commonly used methods of communication in both personal and professional settings. To ensure email security, encryption techniques can be used to protect sensitive information from being intercepted or read by unauthorized parties.
Compliance.
Compliance for cyber security refers to the adherence of an organization to various regulatory guidelines and standards pertaining to information security. Compliance ensures that an organization is taking all necessary measures to safeguard its sensitive data and prevent cyber attacks.
Firewall as a Service.
Firewall as a Service (FWaaS) is a cloud-based solution that provides a comprehensive security framework to businesses for protecting their networks and data from cyber threats. It functions as a virtual barrier that filters out unwanted traffic and unauthorized access attempts, preventing cyber-attacks.



